As the landscape of cybersecurity continues to evolve at a rapid pace, the need for practical, hands-on tools becomes increasingly crucial. One such tool that’s gaining traction in both home networks and educational settings is Pi-hole, a network-wide ad blocker and a powerful resource for enhancing cybersecurity skills.
But Pi-hole is much more than an ad blocker—it’s an invaluable educational tool for cybersecurity enthusiasts and professionals alike. This article will explore the capabilities, benefits, and tremendous potential of Pi-hole in cybersecurity education, highlighting how it serves as a bridge between theoretical concepts and real-world applications.
What is Pi-hole?
Pi-hole is an open-source software that acts as a DNS sinkhole, effectively blocking unwanted content at the network level. Unlike browser-based ad blockers, Pi-hole operates across your entire network. By routing DNS requests through Pi-hole, you can block ads, malware, and tracking domains before they even reach your devices.
Features of Pi-hole
- Network-wide Protection: Once configured, all devices on your network are automatically covered. No need to install software on each device.
- Customizable Block Lists: Users can choose pre-configured block lists or add their own, making Pi-hole incredibly adaptable to individual needs.
- Performance Boost: By blocking unwanted content at the DNS level, network performance is improved, reducing load times and conserving bandwidth.
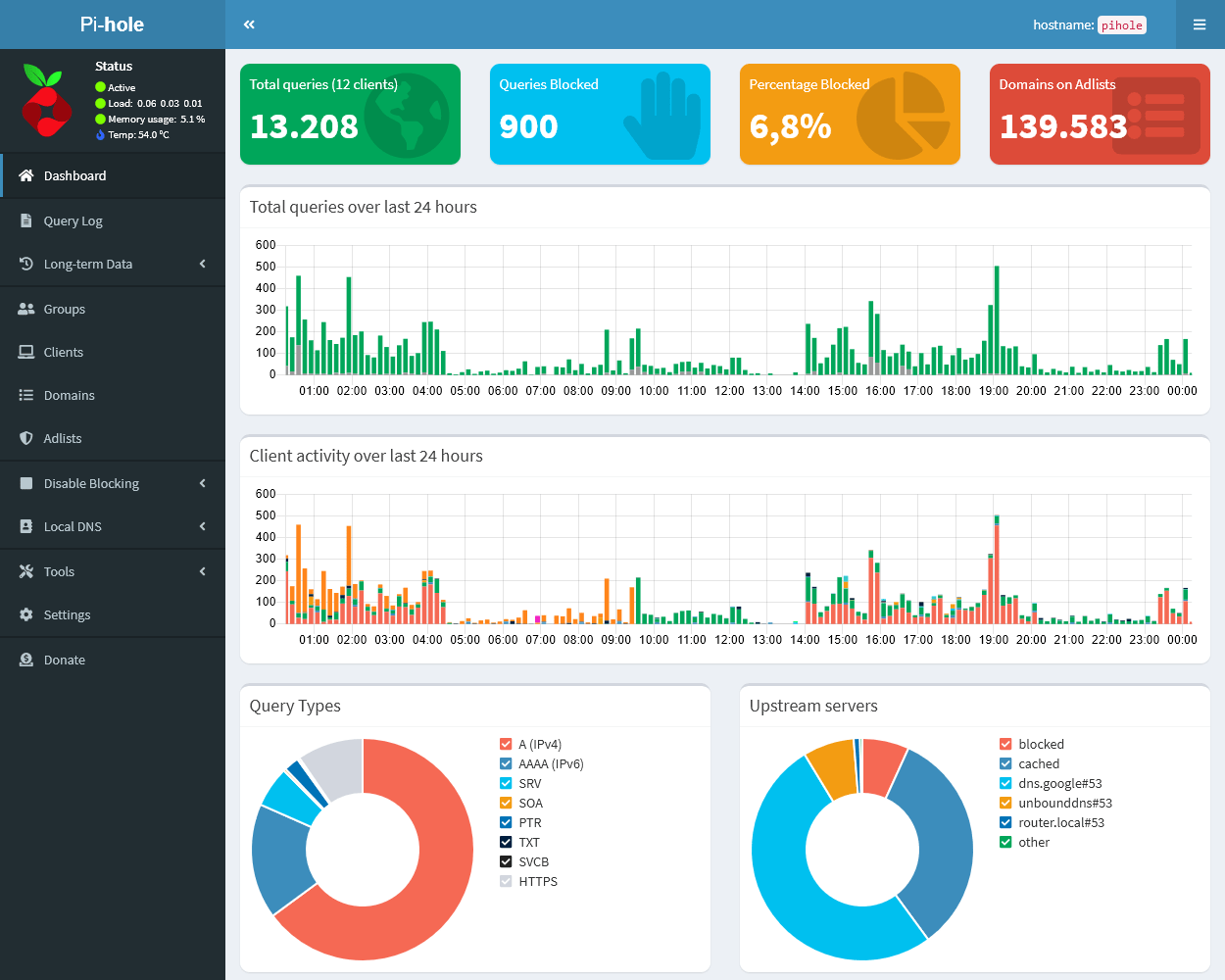
- User-Friendly Interface: Pi-hole includes an intuitive web dashboard, offering an easy way to monitor and control network activity in real time.
The Role of Pi-hole in Cybersecurity Education
Pi-hole isn’t just a utility for blocking ads—it’s a versatile platform for learning cybersecurity fundamentals. Here’s how Pi-hole can play a significant role in developing hands-on skills in network security.
1. Understanding DNS and Network Traffic
DNS (Domain Name System) is a crucial backbone of the internet. Using Pi-hole, students gain hands-on experience with DNS requests and filtering.
- Explore the Flow of DNS Queries: Learn how DNS requests are processed, and practice identifying and blocking malicious domains.
- Visualize Traffic: The Pi-hole dashboard provides real-time data on DNS activity, offering a practical understanding of the data flow in a network.
2. Applying Security Concepts in Practice
Unlike purely theoretical lessons, Pi-hole allows students to actually implement cybersecurity measures.
- Network Configuration: Setting up Pi-hole involves configuring network settings, managing DNS servers, and using the Linux command line, all vital skills in cybersecurity.
- Blocking Malicious Domains: Understand and apply key security concepts like preventing access to known phishing or malicious websites through DNS filtering.
3. Monitoring and Analyzing Network Activity
Network monitoring is a critical skill for cybersecurity professionals. Pi-hole allows students to develop this skill in a controlled and practical environment.
- Threat Detection: Identify potentially harmful domains by monitoring DNS query logs.
- Traffic Trends: Analyze data patterns to understand network activity and detect anomalies.
4. Enhancing Online Privacy
Privacy is an essential pillar of cybersecurity. By blocking tracking domains, Pi-hole protects user data and reduces exposure to online threats.
- Real-World Applications: Hands-on experience with privacy-enhancing tools gives learners a competitive edge when applying for cybersecurity roles.
- Ethical Decision-Making: Explore the role of privacy in cybersecurity and how tools like Pi-hole strengthen user trust.
Getting Started with Pi-hole
Setting up Pi-hole is straightforward, and it’s accessible for learners of all experience levels.
Installation
Pi-hole can be installed on several platforms, including Raspberry Pi, Docker, virtual machines, or even cloud environments. Follow the step-by-step guide linked here to get started:
Configuration
Once installed, you can customize Pi-hole to suit specific needs.
- Add Custom Block Lists: Choose from a variety of pre-configured lists or curate your own for enhanced filtering.
- Integrate with Other Tools: Connect Pi-hole to additional security tools or a VPN for even greater protection.
Maintenance and Updates
To ensure Pi-hole operates optimally, regular updates are essential.
- Update Block Lists: Keep your block lists current to protect against new threats.
- Monitor Performance: Use the web dashboard to monitor usage statistics and make necessary adjustments.
Benefits of Incorporating Pi-hole into Cybersecurity Education
- Hands-On Experience: Pi-hole bridges the gap between theoretical learning and real-world applications, making abstract concepts tangible.
- Adaptable for All Skill Levels: From beginners learning about DNS to advanced users exploring network traffic analysis, Pi-hole caters to a wide range of learners.
- Critical Thinking Development: Encourages students to think critically about network security, privacy, and ethical considerations.
Why Choose Pi-hole for Your Educational Needs?
Pi-hole stands out as a multi-functional tool that is not only cost-effective but also open-source, making it accessible for educational institutions and individuals alike.
- Community Support: With an active user base and extensive online documentation, help is always at hand.
- Scalable: From small practices on Raspberry Pi to enterprise-level configurations, Pi-hole can scale to meet the needs of any user.
Final Thoughts
If you’re looking to develop hands-on skills in cybersecurity, Pi-hole is the perfect tool to begin your journey. By bridging the gap between theory and practice, it provides invaluable insights into DNS management, network security, and online privacy. Whether you’re a student learning the basics or a professional seeking to enhance your skills, Pi-hole offers an engaging and practical learning experience.
Are you ready to unlock the potential of Pi-hole? Start your cybersecurity education today by setting up Pi-hole on your network. Remember—the best way to learn is through DOING