Endpoint Detection and Response (EDR) is a critical component of modern cybersecurity strategies. With the rise of sophisticated cyber threats targeting endpoints such as laptops, servers, and mobile devices, EDR tools help detect, analyze, and respond to potential risks in real-time. However, managing EDR alerts can often feel overwhelming due to the sheer volume of notifications generated in an enterprise environment.
This post will explore the most common categories of EDR alerts, provide examples of key alerts organizations typically encounter, and share best practices for analyzing, prioritizing, and responding effectively. Whether you’re a security analyst working in a SOC or an IT professional overseeing endpoint security, this guide will help you navigate the EDR alert landscape with confidence.
Why EDR Alerts Matter
Why are EDR alerts so critical to an organization’s security posture? Simply put, endpoints are common entry points for attackers. Malicious actors often use techniques such as phishing emails, malware, or compromised credentials to gain access to endpoints before moving laterally across a network.
EDR tools monitor endpoint activities, log suspicious behaviors, and send alerts when potential threats are detected. These alerts highlight risks such as malware infections, unauthorized file access, and anomalous network behavior. Ignoring or mismanaging these alerts could allow attackers to escalate their operations undetected, causing significant damage to your business.
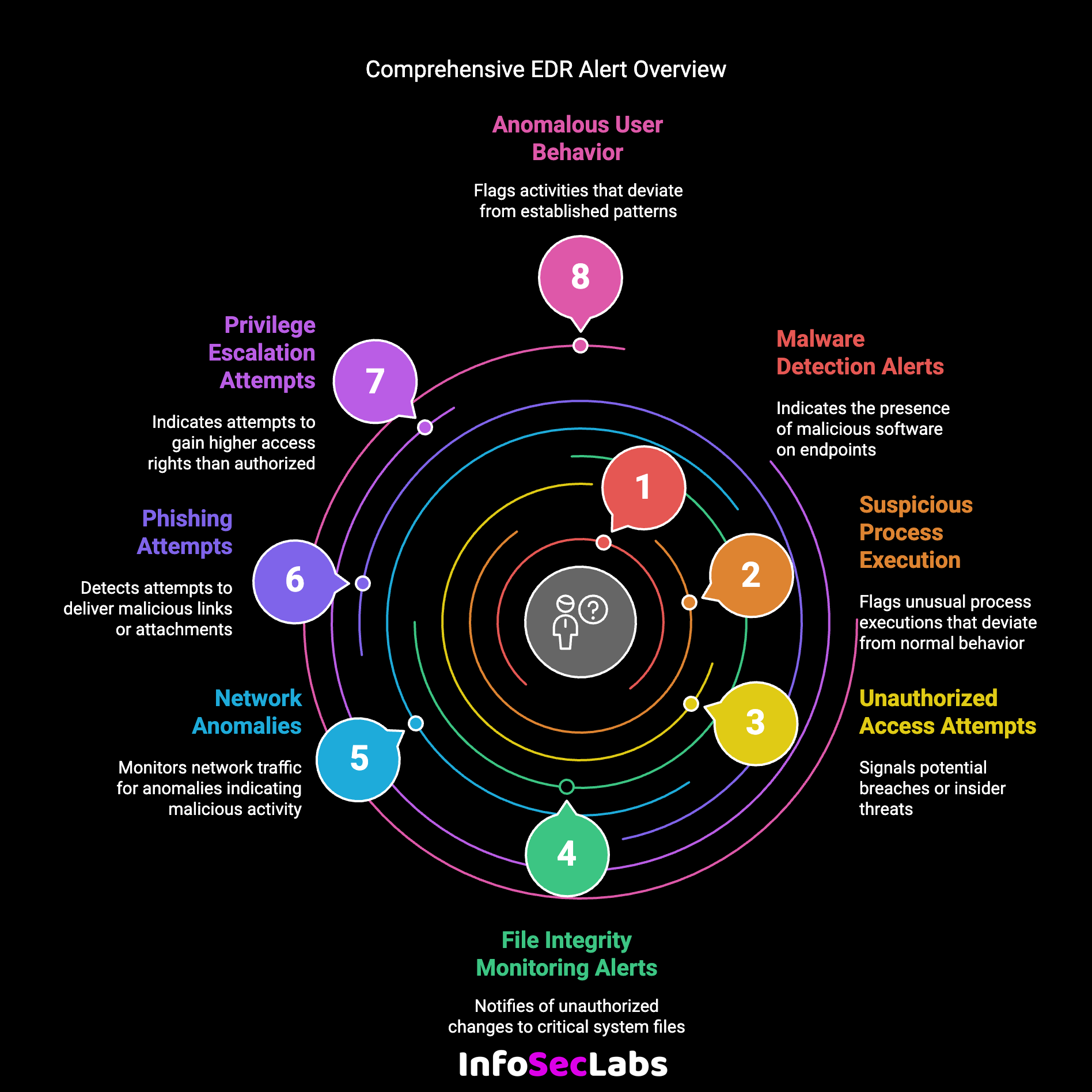
Common EDR Alert Categories
To efficiently manage EDR alerts, it’s important to first understand their key categories. These alerts typically fall under the following types:
1. Malware Detection
Alerts related to known or suspected malware activity, such as ransomware, trojans, or spyware. These often stem from signature-based detections or anomalous behaviors.
2. Suspicious Process Execution
Alerts generated when an unusual or unauthorized process runs on an endpoint. Examples include PowerShell abuse or launching a process from unexpected directories.
3. Unusual User Behavior
Behavioral anomalies such as a user accessing sensitive data at unusual hours or failed login attempts from unfamiliar locations often trigger alerts.
4. File Integrity Variations
Activities such as unauthorized changes, additions, or deletions of critical system files or registries send file integrity alerts. These can indicate attempts to tamper with systems.
5. Network Anomalies
Unusual traffic patterns between endpoints or outbound connections to suspicious external IP addresses result in network-related alerts.
6. Privilege Escalation Attempts
Alerts flagging actions where a user or process attempts to gain elevated access privileges without authorization.
Top EDR Alert Examples (with Samples)
Let’s take a closer look at specific EDR alert examples and their significance in an enterprise security environment.
Example 1: Ransomware Behavior Detected
- Alert Description: Files are being renamed with “.encrypted” extension, indicating potential ransomware activity.
- Details:
-
- Process Name:
encryptor.exe - Detected Behavior: Mass file encryption in user directories.
- Host Machine:
Workstation-22
- Process Name:
- Action Required:
-
- Isolate the endpoint immediately.
- Identify the ransomware strain and retrieve backups.
- Perform a root-cause analysis to prevent recurrence.
Example 2: PowerShell Command-Line Anomaly
- Alert Description: Unusual PowerShell script execution detected on server.
- Details:
-
- Command Line Argument:
powershell -exec bypass -enc [Base64 encoded payload] - User Account:
admin_temp - Timestamp:
2024-03-14 11:23 PM
- Command Line Argument:
- Action Required:
-
- Investigate execution context and user activity.
- Reverse engineer the encoded payload to detect malicious intent.
Example 3: Unauthorized Administrator Access
- Alert Description: A non-admin user attempted to access privileged directories.
- Details:
-
- Affected Directory:
/etc/shadow - Failed Logins Detected: 5 attempts
- Source IP Address:
192.168.1.45
- Affected Directory:
- Action Required:
-
- Lock the user’s account temporarily.
- Analyze source IP activity for brute-force attack patterns.
Example 4: Outbound Connection to Known Malicious IP
- Alert Description: Host attempted to contact a blacklisted external IP address.
- Details:
-
- External IP Address:
185.83.188.1 - Host Device:
Desktop-07 - Application Name:
SysMain.exe
- External IP Address:
- Action Required:
-
- Block IP in firewall.
- Check endpoint for potential command-and-control (C2) channel activity.
Example 5: Registry Tampering Alerts
- Alert Description: Registry key modification flagged as suspicious.
- Details:
-
- Registry Key Path:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run - Change Detected: Addition of
malicious.exereference for persistence. - Trigger Time:
2024-03-15 9:00 AM
- Registry Key Path:
- Action Required:
-
- Revert registry changes.
- Investigate the origin of
malicious.exe. - Perform endpoint-wide malware scanning.
Analyzing and Prioritizing EDR Alerts
Not every alert is mission-critical. A common mistake security analysts make is treating all alerts as equal. Instead, it’s essential to evaluate and prioritize alerts based on the following factors:
- Severity: Focus first on high-severity alerts that indicate immediate threats, such as active ransomware or privilege escalation.
- Context: Consider the environment in which the alert occurred. For example, registry tampering might be more critical on a domain controller than a workstation.
- Correlation: Use threat intelligence feeds and EDR correlation features to identify whether an alert is part of broader malicious behavior.
Best Practices for Responding to EDR Alerts
Proper response strategies can make or break an organization’s ability to handle threats effectively. Consider adopting these best practices for EDR alert management:
Automate Where Possible
Leverage the automation features in your EDR solution to remediate low-severity alerts (e.g., quarantining files) while focusing analysts on advanced threats.
Create Runbooks
Develop and refine incident response runbooks for common threats like ransomware, unauthorized access, and phishing attempts, ensuring consistent reactions across your team.
Establish Clear Escalation Paths
Outline which alerts need to be escalated to senior teams or external responders. For example, DDoS attacks might warrant involving a managed security service provider (MSSP).
Regularly Train SOC Teams
EDR tools are only as effective as the professionals monitoring them. Conduct regular training sessions to keep SOC teams updated on the evolving threat landscape.
Leverage Threat Intelligence
Integrate external threat feeds into your EDR platform to provide additional context for alerts, helping you differentiate between benign activity and active threats.
Strengthen Your Approach to EDR Today
Managing EDR alerts effectively is essential to every organization’s cybersecurity strategy. By understanding common alert categories, focusing on high-priority threats, and implementing best practices for response, you can significantly reduce your attack surface and improve your security posture.
Above all, remember that EDR is not a standalone solution. Combining it with endpoint protections like antivirus, firewalls, and experienced SOC support ensures comprehensive protection.
Looking to enhance your alert management process? Consider exploring advanced EDR solutions tailored to your organization’s needs.