The world of cybersecurity is vast, continuously evolving, and demanding. Whether you’re a seasoned professional or a budding enthusiast, having the right tools can be a game-changer. One such tool that’s been making waves in the cybersecurity community is Kasm Workspaces. But what exactly is it, and how can you incorporate it into your home lab to enhance your skills and security? This blog will answer these questions and guide you through using Kasm Workspaces as a cybersecurity professional.
What is Kasm Workspaces?
Overview of Kasm Workspaces
Kasm Workspaces is a modern, container-based virtual desktop infrastructure (VDI) platform designed to create isolated environments for safe browsing, application deployment, remote work, and more. Unlike traditional VDIs, Kasm Workspaces utilizes lightweight containers, such as Docker, to provide scalable and secure access to virtualized environments.
Whether you need to run a browser in a sandboxed environment, analyze suspicious files isolated from your main machine, or simply access a secure workspace remotely, Kasm Workspaces offers a robust and efficient solution.
Benefits for Cybersecurity Professionals
For cybersecurity professionals, Kasm Workspaces checks several critical boxes:
- Secure Environments: Create isolated containers to analyze threats, execute potentially malicious files, or browse the web securely without risk to host machines.
- Lightweight and Scalable: Unlike resource-heavy VMs, Kasm Workspaces’ containerized approach provides flexibility without high hardware requirements.
- Centralized Management: Manage multiple workspaces, configurations, and users from a single dashboard effortlessly.
- Cross-Platform Availability: Use it on any operating system or even access it directly via a browser, ensuring compatibility with your existing setup.
- Enhanced Privacy: By utilizing ephemeral containers, your browsing session or workspace can be reset entirely once closed.
Setting Up Kasm Workspaces in a Home Lab Environment
Building a secure and efficient home lab is essential for cybersecurity professionals looking to hone their skills. Follow this step-by-step guide to install and configure Kasm Workspaces within your home environment.
Step 1: System Requirements
Before you start, ensure your machine meets the following minimal requirements:
- CPU: Modern 4+ core processor (more cores improve multi-container performance).
- RAM: Minimum 8GB, though 16GB+ is recommended for running multiple containers simultaneously.
- Storage: At least 50GB of free space to store container images and logs.
- Operating System: Linux-based systems like Ubuntu or CentOS are recommended, but support for Docker allows for flexibility.
Step 2: Download and Install
- Download Kasm Workspaces Installer: Head to the official Kasm website, create an account, and download the latest community edition.
- Install Docker: Since Kasm Workspaces relies on Docker, ensure you have Docker installed. Use the command:
sudo apt-get install docker.io
- Run the Installer: Execute the installation script with:
sudo bash kasmrelease.sh
- Access the Admin Interface: Once installed, you can access Kasm Workspaces via its web-based admin panel at
http://<YOUR-IP>:443.
Step 3: Configure Your Workspaces
- Log into the Admin Panel: Use the default credentials provided during installation (you’ll be prompted to change your password).
- Create Workspaces: Choose from pre-configured workspaces such as secure browsers, developer tools, or custom containers for cybersecurity analysis.
- Adjust Resource Allocations: Depending on your system, tweak CPU and RAM settings assigned to containers for optimal performance.
Step 4: Test and Explore
Once configured, start your first workspace! Experiment with its features, and test secure browsing or isolated file executions to get familiar with the environment.
Use Cases for Kasm Workspaces in Cybersecurity
Now that your Kasm Workspaces setup is up and running, let’s explore practical applications for cybersecurity professionals.
1. Secure Browsing
One of the most significant challenges in cybersecurity is dealing with malicious websites. Kasm Workspaces allows you to browse the web through isolated containers, ensuring that any scripts or malware remain sandboxed and do not affect your system.
2. Threat Analysis
Analyze suspicious files in a Kasm container without worrying about infecting your host machine. For instance, upload a potentially malicious PDF or executable to determine its behavior without endangering your primary operating system.
3. Training Simulated Attacks
Run cybersecurity drills by simulating attacks in a controlled Kasm environment. You can use containerized tools like Metasploit or Wireshark to practice detecting and mitigating threats in real-time.
4. Team Collaboration
Kasm Workspaces supports multi-user environments, making it easy to collaborate with team members during incident response or analysis. Share logs, findings, and configurations quickly without exposing sensitive data.
5. Remote Work
Access your workspaces from anywhere. Whether you’re outside the office or just prefer to work remotely, Kasm allows you to connect securely to your environments through a simple browser interface.
6. Advanced Research
With customizable containers, Kasm enables you to build workspaces tailored for specific types of research, such as penetration testing, malware reverse engineering, or OSINT investigations.
Advanced Configurations and Security Considerations
To maximize the effectiveness of Kasm Workspaces in a cybersecurity context, consider these advanced tips and security measures.
Regular Updates
Always keep your Kasm Workspaces installation up to date to benefit from the latest security patches and feature improvements. Use the apt update and kasm_updater.sh scripts frequently.
Network Segmentation
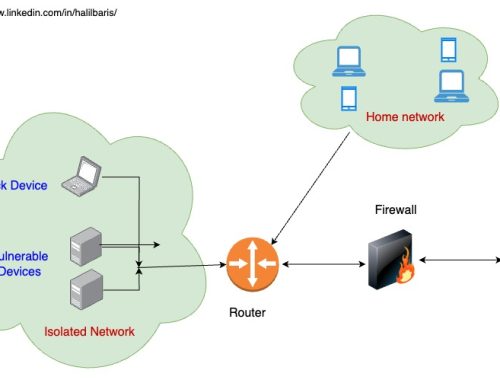
For added security within your home lab, isolate Kasm Workspaces using VLANs or dedicated subnets. This ensures potentially malicious activity in containers does not spill over into your broader network.
Custom Containers
While Kasm includes many pre-configured containers, you can create custom ones tailored to your specific use cases. For example, build containers with the tools you frequently use, such as Burp Suite or Kali Linux.
Access Controls
Use Kasm’s built-in role-based access control (RBAC) to manage permissions if several users share your setup. Limit admin-level access and enforce policies that prevent unauthorized modifications.
Monitoring and Logging
Leverage Kasm’s logging features to monitor container activities. You can integrate these logs into SIEM tools in your home lab setup, enabling better visibility and analytics.
Elevate Your Cybersecurity Skills with Kasm Workspaces
Kasm Workspaces is more than just a productivity tool; it’s a powerhouse for cybersecurity professionals and enthusiasts alike. From providing secure, isolated environments to enabling advanced threat analysis, Kasm opens the door to safe experimentation and hands-on learning experiences.
Whether you’re a professional fine-tuning your skills or a hobbyist building your first home lab, Kasm Workspaces delivers unparalleled flexibility and security. Equipped with its advanced features and easy configurability, you’ll find yourself prepared to tackle increasingly complex cybersecurity challenges.