Need to Know
If you want to deep dive into cybersecurity you must know common knowledge about these articles

Understanding DDoS Attacks Methods Tools and Mitigation Strategies
May 25, 2025
4 min
Distributed Denial-of-Service (DDoS) attacks have become one of the most significant threats in the digital era. They[...]

What is Zero Trust Architecture A Simple Overview
May 23, 2025
4 min
Cybersecurity threats are becoming increasingly sophisticated. Traditional security models, centered on the idea of creating a secure[...]

Security Alarms Don’t Just See Understand
May 21, 2025
4 min
When was the last time your security team investigated an alarm and discovered its actual cause? Security[...]

Beyond Signatures – Why Your Antivirus Isn’t Enough and EDR is the Future
May 18, 2025
5 min
Cyberattacks are becoming increasingly sophisticated, targeting vulnerabilities with precision and speed. For years, traditional antivirus solutions have[...]

Kasm Workspaces for Cybersecurity Professionals: A Guide to Setup and Use in Home Labs
May 9, 2025
5 min
The world of cybersecurity is vast, continuously evolving, and demanding. Whether you're a seasoned professional or a[...]

AI-Powered Cyberattacks: How Hackers Are Using Machine Learning
May 8, 2025
5 min
The rapid advancements in artificial intelligence (AI) have revolutionized industries, streamlining processes and creating new opportunities. But[...]

Security Tools vs. Manual Investigation: Building a Balanced Cybersecurity Professional
May 7, 2025
5 min
Cybersecurity is one of the most dynamic fields in the modern workforce, where threats evolve as quickly[...]

How to Protect Yourself From Pineapple Attacks
May 6, 2025
5 min
When you hear the term "Wi-Fi Pineapple," you might picture a tropical fruit connected to your network—but[...]
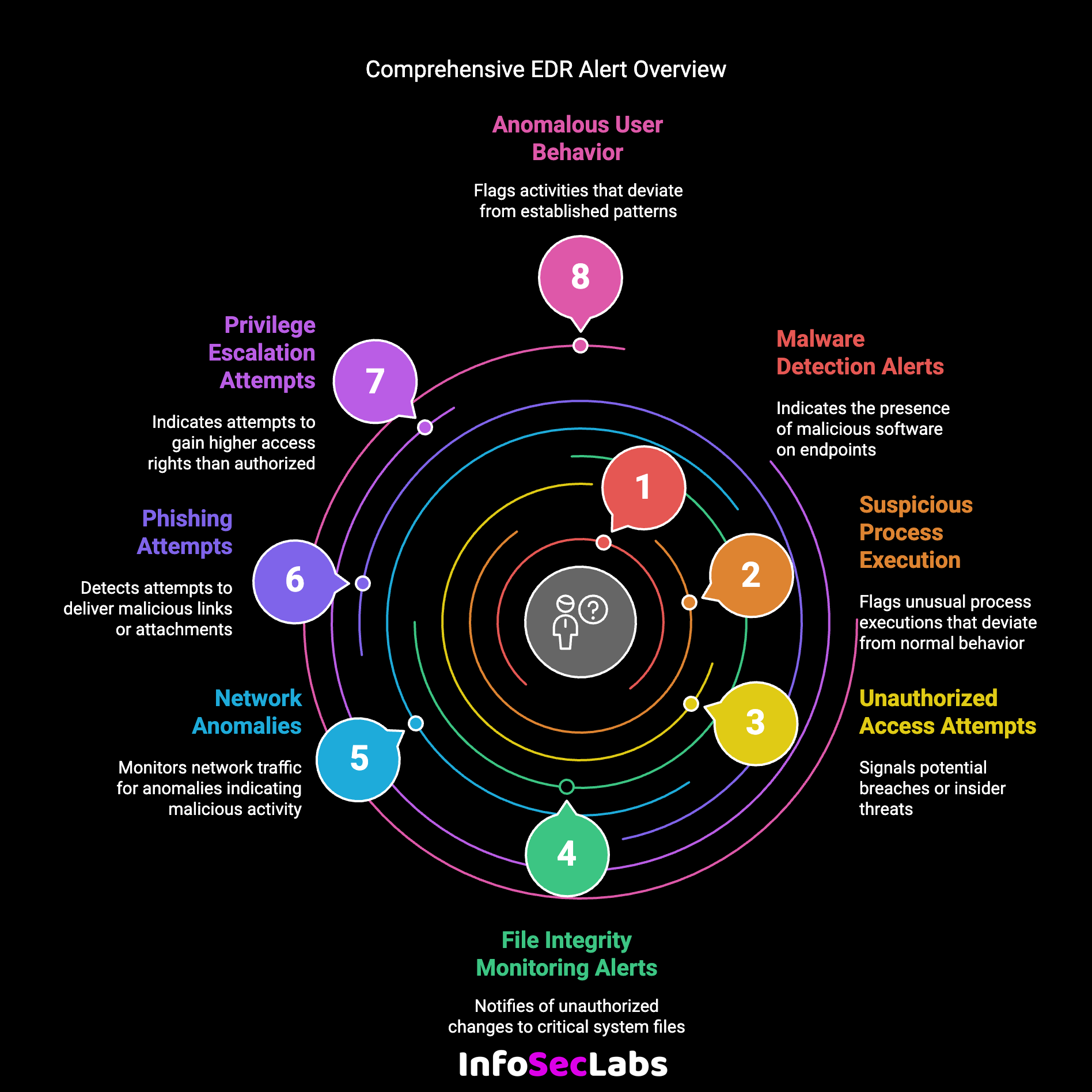
Top EDR Alerts Every Organization Encounters and How to Handle Them
April 22, 2025
5 min
Endpoint Detection and Response (EDR) is a critical component of modern cybersecurity strategies. With the rise of[...]
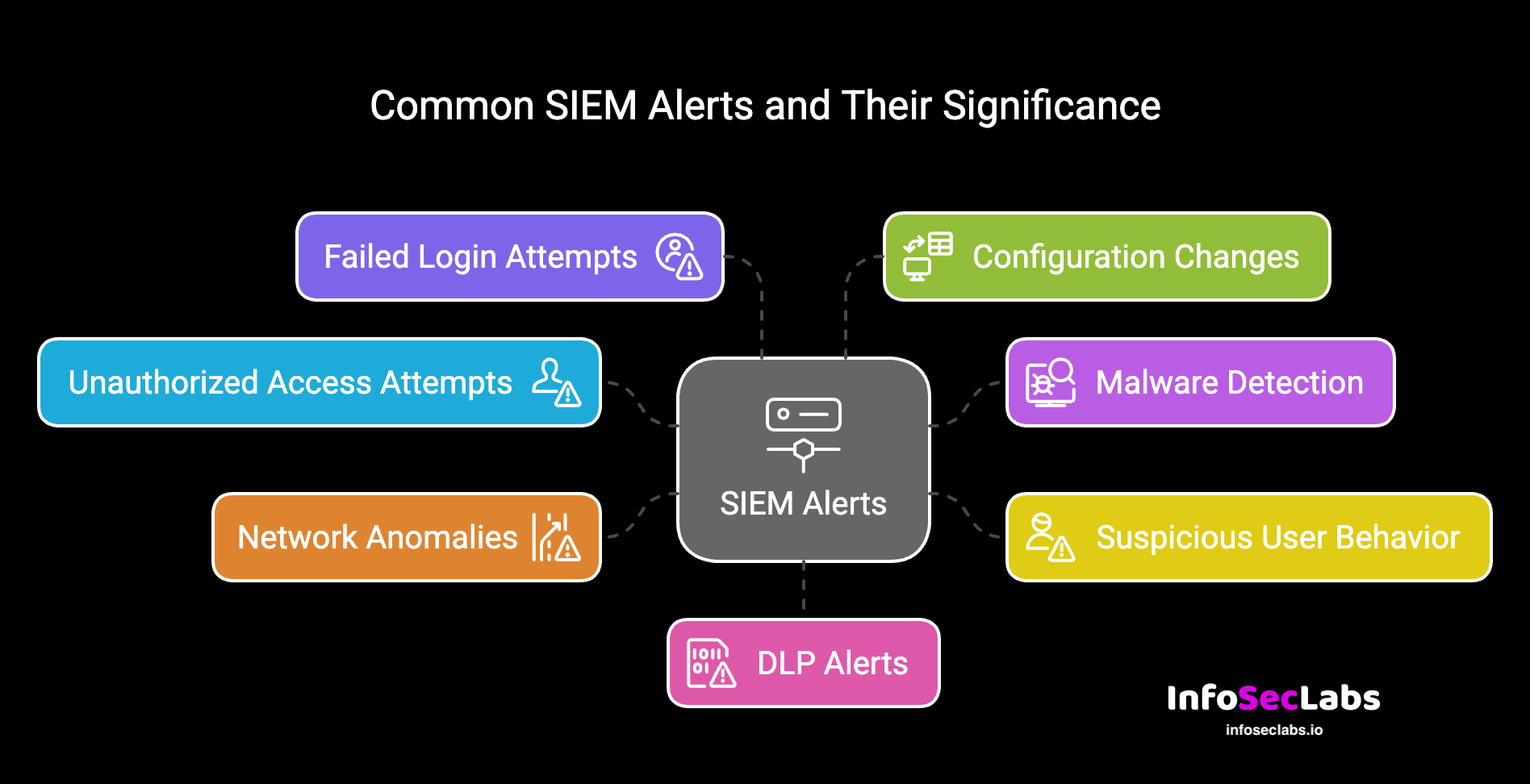
Top SIEM Alerts Organizations Receive
April 21, 2025
6 min
Security Information and Event Management (SIEM) systems are foundational tools in modern cybersecurity. They provide critical insights[...]

What Hackers Know That You Don’t
April 16, 2025
3 min
The digital world is buzzing with activity. Everywhere we go, invisible connections through Wi-Fi, Bluetooth, and other[...]

Breaking Into Cybersecurity: A Realistic Guide for Aspiring Professionals
April 14, 2025
5 min
Entering the field of cybersecurity is one of the most exciting career paths in tech, but it’s[...]

Are Smart Homes Safe? The Hidden Risks of IoT Security
April 14, 2025
6 min
Smart homes are no longer a futuristic dream; they're now a part of everyday life. From smart[...]

Deepfakes and Cybersecurity Risks: What You Need to Know
April 9, 2025
5 min
With AI rapidly evolving, deepfakes have transitioned from simple internet curiosities to major cybersecurity threats. Their ability[...]

How will emerging technologies impact cybersecurity?
March 24, 2025
5 min
The cybersecurity landscape is evolving faster than ever before, fueled by rapid technological advancements and an expanding[...]

Alternative Careers in Cybersecurity Beyond Pentesting
March 23, 2025
4 min
Cybersecurity is often synonymous with pentesting (penetration testing). It’s an exciting career that involves identifying vulnerabilities in[...]

What You Should Learn Before Starting a Career in Cybersecurity
March 20, 2025
5 min
Are you intrigued by the dynamic world of cybersecurity but unsure how to take the first step?[...]

Is Flipper Zero a Good Starting Point for Cybersecurity? Plus Beginner Tips
March 17, 2025
5 min
If you're just venturing into the vast world of cybersecurity, you've probably come across the term "Flipper[...]

Why Every Organization Needs an Incident Response Plan for Cybersecurity
March 16, 2025
5 min
What Is an Incident Response Plan (IRP) and Why Does Your Business Need One? In today’s fast-paced[...]

The Impact of AI on Cybersecurity: Opportunities and Threats
March 15, 2025
5 min
Artificial intelligence (AI) is transforming industries across the globe, and cybersecurity is no exception. From enhancing threat[...]

How Cybersecurity Professionals Can Detect Advanced Persistent Threats (APTs)
March 10, 2025
5 min
Advanced Persistent Threats (APTs) are among the most sophisticated and potentially devastating cyber threats faced by organizations[...]

How to Defend Your Organization Against Script Kiddies
March 9, 2025
6 min
Cyberthreats come in all shapes and sizes, but one often underestimated group of attackers is the script[...]

What is Zero Trust Security, and Why Does It Matter?
March 8, 2025
6 min
Cyber threats are evolving at an unprecedented pace, with bad actors finding new ways to infiltrate even[...]

Top 10 Things Every SOC Analyst Should Know Inside Out
March 5, 2025
5 min
The role of a Security Operations Center (SOC) Analyst is one of vigilance, adaptability, and expertise. A[...]

Exploring Open Source Tools for Cybersecurity Professionals
March 3, 2025
5 min
The cybersecurity landscape is dynamic, challenging, and undeniably vital in today’s technology-driven world. Whether you're an aspiring[...]

How to Become the Best Cybersecurity Professional
March 1, 2025
4 min
The global demand for cybersecurity professionals is soaring. With cyberthreats becoming more sophisticated every day, the need[...]

Secure Your Wi-Fi: Tips for a Stronger Network at Home
February 27, 2025
5 min
Your home Wi-Fi network is more than just an internet connection—it’s the gateway to personal data, banking[...]

Anatomy of a Phishing Attack: How to Recognize the Signs
February 27, 2025
6 min
Phishing attacks are one of the most common cybersecurity threats affecting businesses today. Whether it’s a cleverly[...]

How Security Operations Center (SOC) Uses Threat Intelligence
February 26, 2025
5 min
A cyber security operations center nowadays can be compared to a military headquarters. Although defense-oriented, it needs[...]

Firewalls vs. Next-Generation Firewalls (NGFW): What Cybersecurity Professionals Need to Know
February 25, 2025
5 min
Cyber threats are evolving at an unprecedented pace, targeting businesses of all sizes and industries. At the[...]

Cybersecurity for Small Businesses: Affordable Best Practices
February 25, 2025
5 min
Running a small business comes with its fair share of challenges—tight budgets, fierce competition, and limited resources.[...]

AI-Generated Malware: Rising Cybersecurity Threats and How to Defend Against Them
February 23, 2025
3 min
Artificial Intelligence (AI) is revolutionizing sectors like healthcare and finance, but it’s also making waves in the[...]

Introduction to Penetration Testing: Tools and Techniques
February 20, 2025
4 min
Cybersecurity is no longer optional—it's essential. With cyberattacks growing more sophisticated, penetration testing (or “pen testing”) has[...]

Finding WEIRD Devices on the Public Internet
February 19, 2025
3 min
Have you ever wondered how many peculiar or unexpected devices are accessible on the public internet? From[...]
10 Common Cyber Threats and How to Mitigate Them
February 18, 2025
5 min
Cyber threats are constantly evolving, and they can have devastating consequences for businesses, governments, and individual users[...]

Security Tool Analyst vs. Security Alerts Without Tools: Which Approach is Best?
February 17, 2025
5 min
Cybersecurity is a rapidly evolving field, where protecting digital assets is critical for organizations of all sizes.[...]

Most Common Cybersecurity Alerts in Organizations
February 17, 2025
5 min
Cyber threats are on the rise, and organizations face a constant battle to secure their systems. One[...]
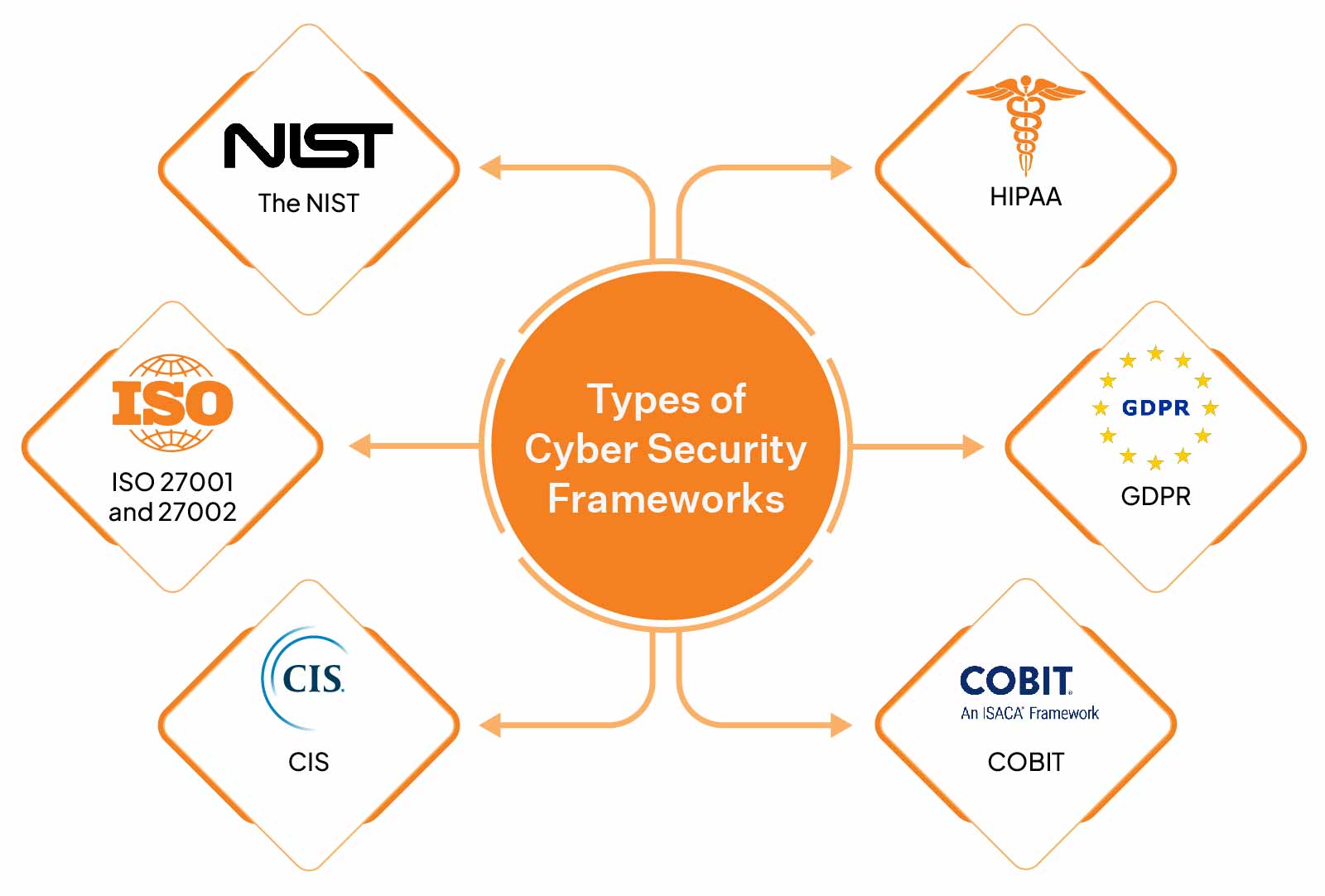
Understanding Cybersecurity Frameworks: NIST, ISO, and More
February 16, 2025
5 min
Cybersecurity remains a top priority for businesses and individuals in an increasingly digital world. However, understanding how[...]

The Truth About Starting a Career in Cybersecurity with Bootcamp
February 15, 2025
5 min
The field of cybersecurity has gained immense popularity in recent years, and with good reason. From protecting[...]

The Basics of Cyber Hygiene: How to Stay Safe Online
February 14, 2025
4 min
The internet has become an essential part of daily life, powering everything from personal interactions to professional[...]

Is AI Saving or Taking Jobs? Exploring the Impact on Work and Cybersecurity
February 13, 2025
4 min
The world constantly evolves with technological advancements, and artificial intelligence (AI) is at the forefront of this[...]
Cyberbullying and Blackmail: The Dark Web’s Disturbing Business Model
February 13, 2025
5 min
Behind the veil of anonymity, the dark web has evolved into a breeding ground for malicious activities[...]

How to Protect Your Website from DDoS Attacks
February 12, 2025
4 min
With the rise of internet dependency, the risk of cyberattacks continues to grow. Among the most disruptive[...]

The Young Hacker Who Breached a Government System: Lessons for Aspiring Cybersecurity Enthusiasts
February 11, 2025
5 min
With technology at the core of our daily lives, we often forget how small—almost invisible—vulnerabilities can lead[...]

The Dark Side of Gaming: How Virtual Worlds Are Fuels for Cybercrime
February 10, 2025
3 min
When the world turned to virtual entertainment for solace during the COVID-19 pandemic, another global phenomenon quietly[...]

How to Protect Your Business from Insider Threats
February 10, 2025
4 min
Insider threats pose a serious, often underestimated risk to businesses of all sizes. These security challenges come[...]

Tips for Keeping Your Social Media Accounts Secure
February 8, 2025
4 min
Social media platforms have become an integral part of both our personal and professional lives. From sharing[...]

Identifying and Mitigating Vulnerabilities in Organizational Cybersecurity
February 6, 2025
5 min
Modern organizations heavily rely on technology to drive operations, foster communication, and spark innovation. However, with technological[...]

SIEM vs. EDR: Which Tools Matter Most in an Organization’s Cybersecurity Framework?
February 4, 2025
5 min
Cybersecurity is pivotal for modern organizations. With evolving threats, having the right tools in place is paramount.[...]

Why Practice is Essential to Master Cybersecurity
February 3, 2025
5 min
Earning certifications is often the first step for aspiring cybersecurity professionals, but it’s not the final step.[...]

5 Must-Know Sysinternals Tools for Cybersecurity Professionals
February 2, 2025
4 min
When it comes to safeguarding systems and detecting threats, the right tools can make all the difference.[...]

Break Into Cybersecurity and Overcome Rejections
January 31, 2025
4 min
Breaking into cybersecurity can be challenging, especially if you're just starting out and facing rejection after rejection.[...]

7 Cybersecurity Tips Easy to Do
January 30, 2025
5 min
When it comes to protecting yourself online, many people stick to the basics—strong passwords, two-factor authentication (2FA),[...]

The Fastest Way to Learn Cloud Security
January 27, 2025
5 min
The demand for cloud security professionals has never been greater. With the cloud computing market projected to[...]

Why Isolating End-of-Life (EOL) Systems is Critical for Cybersecurity
January 27, 2025
5 min
In an ideal world, businesses would always operate on up-to-date, secure, and supported software. The reality, however,[...]

How to Perform a Basic Vulnerability Assessment
January 26, 2025
4 min
Cybersecurity threats are evolving, targeting organizations and individuals alike. Conducting a thorough vulnerability assessment is a crucial[...]

Cybersecurity in the Healthcare Industry
January 26, 2025
4 min
Why Cybersecurity Matters in Healthcare The healthcare industry handles some of the most sensitive and personal data—patients'[...]

How Can AI Transform Cybersecurity? Use Cases and Insights
January 25, 2025
4 min
The rise of digitalization has brought an increasing number of sophisticated cyber threats. For IT professionals, cybersecurity[...]
Top Linux Distributions and Virtual Machines for Cybersecurity Professionals
January 23, 2025
4 min
Cybersecurity is a rapidly evolving field that requires a specialized set of tools and environments to perform[...]

10 Best Careers in Cybersecurity for 2025
January 23, 2025
5 min
Cybersecurity has become a crucial field in today’s internet-driven world, and its importance will only grow as[...]

Understanding the Originating Process in Cybersecurity
January 23, 2025
4 min
When a cybersecurity incident occurs, getting to the root cause is crucial. One of the most significant[...]

Which is Better for You? A Detailed Comparison of Kali Linux vs. Parrot OS
January 23, 2025
5 min
Choosing the right operating system is critical for cybersecurity professionals and privacy advocates. When it comes to[...]

Unlocking Identity Threat Detection and Response in Cybersecurity
January 23, 2025
5 min
With the growing prevalence of credential-based cyberattacks, protecting digital identities has become a critical priority for businesses.[...]

The Importance of Cybersecurity Awareness Training
January 23, 2025
4 min
Cybersecurity threats are becoming more sophisticated, diverse, and frequent. With the rise of cybercrime—from phishing emails to[...]
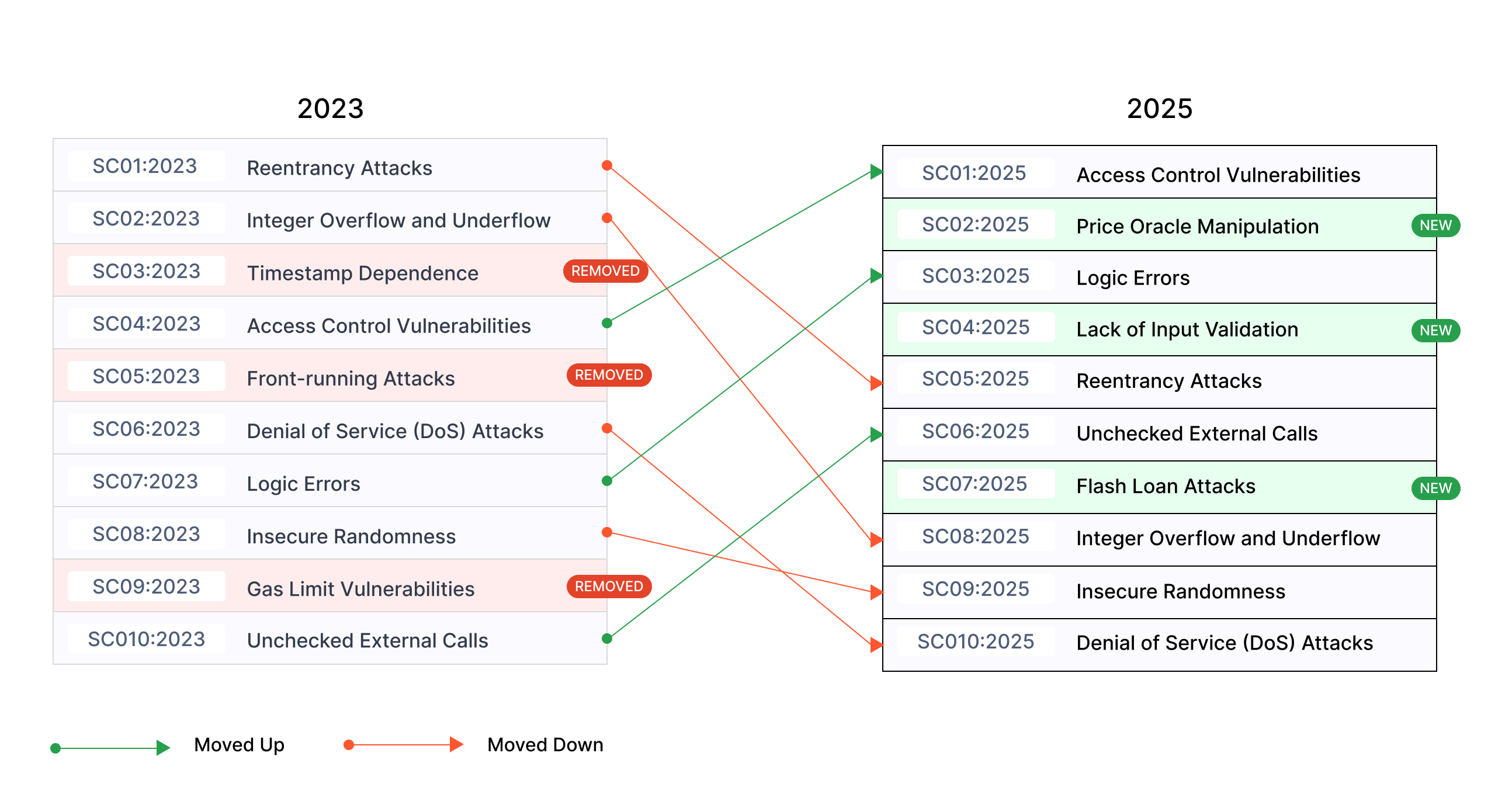
OWASP Top 10 Smart Contract Vulnerabilities for 2025
January 21, 2025
4 min
Smart contracts lie at the heart of blockchain innovation, enabling decentralized applications (dApps) and seamless transactions. However,[...]

How to Become Invisible on the Internet with Whonix
January 21, 2025
5 min
As the digital age advances, online privacy is becoming more critical than ever. Cybersecurity threats are rampant,[...]

How to Become a SOC Analyst in 2025
January 21, 2025
5 min
If you're passionate about cybersecurity and eager to start an impactful career, becoming a Security Operations Center[...]

The Evolution of Cyber Attacks: A Historical Perspective
January 21, 2025
5 min
Cybersecurity is no longer an optional consideration for businesses or individuals—it’s essential. With every advancement in technology,[...]

15 Best Cybersecurity Tools You Need to Know in 2025
January 19, 2025
7 min
Cybersecurity isn’t just a choice anymore—it’s a necessity. With cyberattacks growing more sophisticated each year, protecting sensitive[...]

How to Create a Cyber Incident Response Plan
January 19, 2025
5 min
Cybercrime is on the rise, impacting organizations of all sizes. With cyber threats becoming increasingly sophisticated, adopting[...]
A Comprehensive Guide to Computer Viruses and How to Stay Safe
January 18, 2025
3 min
Computer viruses are an ever-present threat in our digital lives. Just like biological viruses, they spread fast,[...]

The Future of Cybersecurity: Trends to Watch in 2025 and Beyond
January 17, 2025
4 min
The digital landscape continues to evolve at breakneck speed, and with it come new challenges and opportunities[...]

VPN Basics: Understanding How VPNs Work and Why They’re Essential for Public Networks
January 16, 2025
4 min
Technology enthusiasts and cybersecurity professionals alike recognize the importance of staying protected online. This is where Virtual[...]
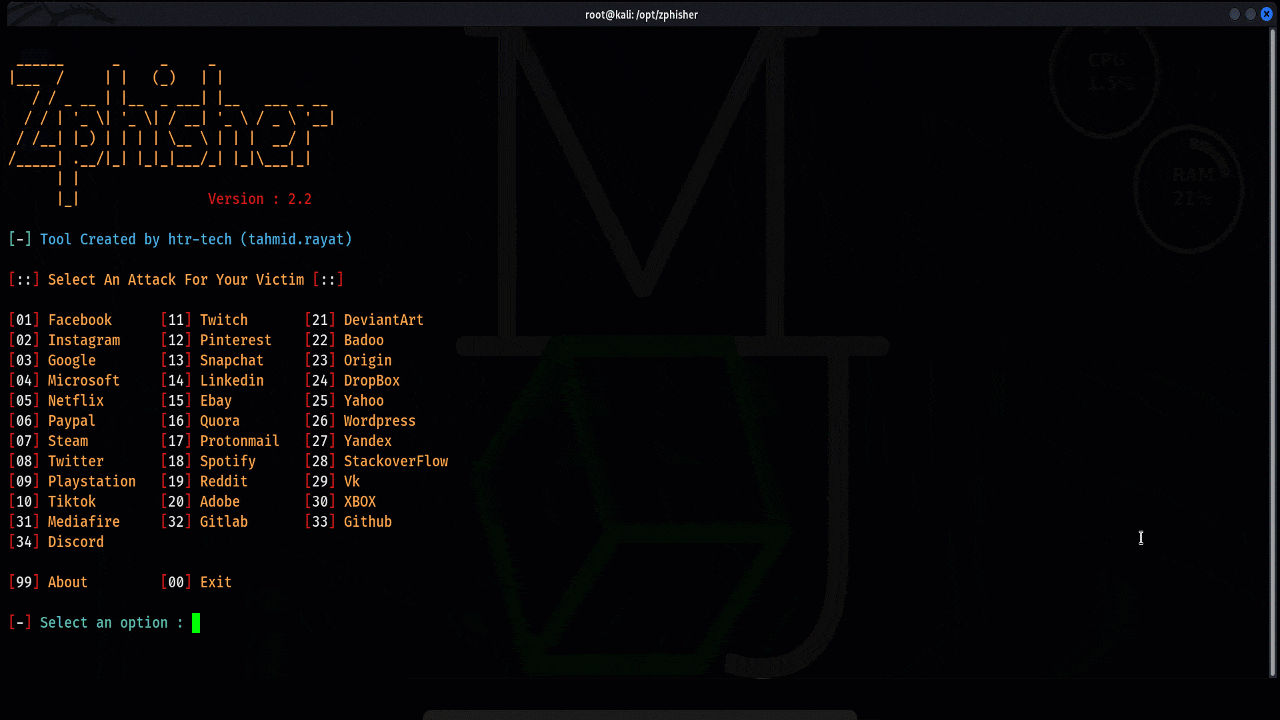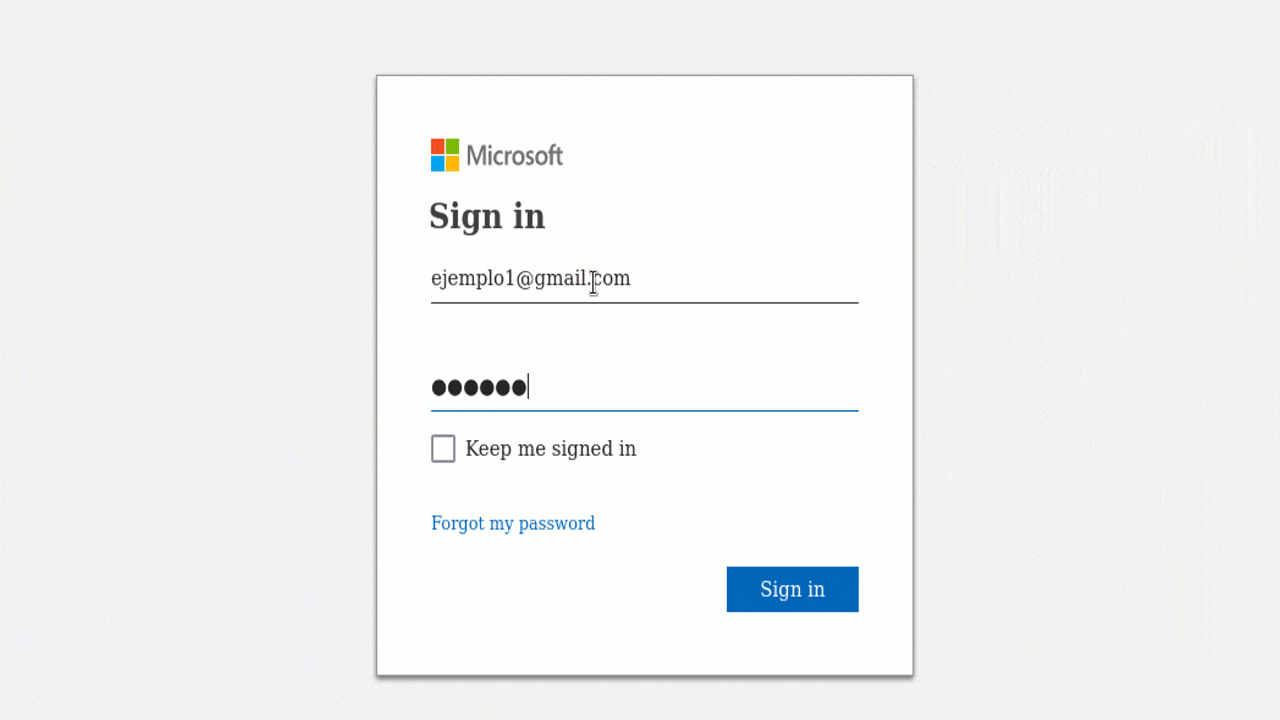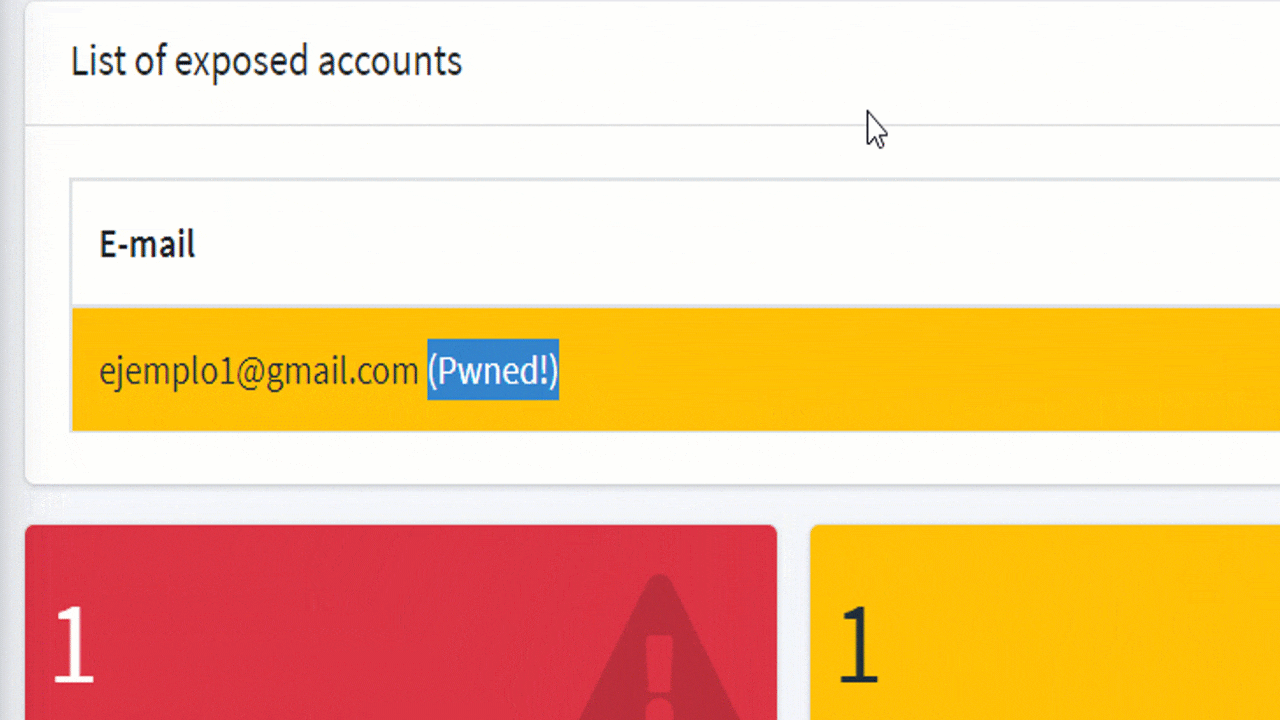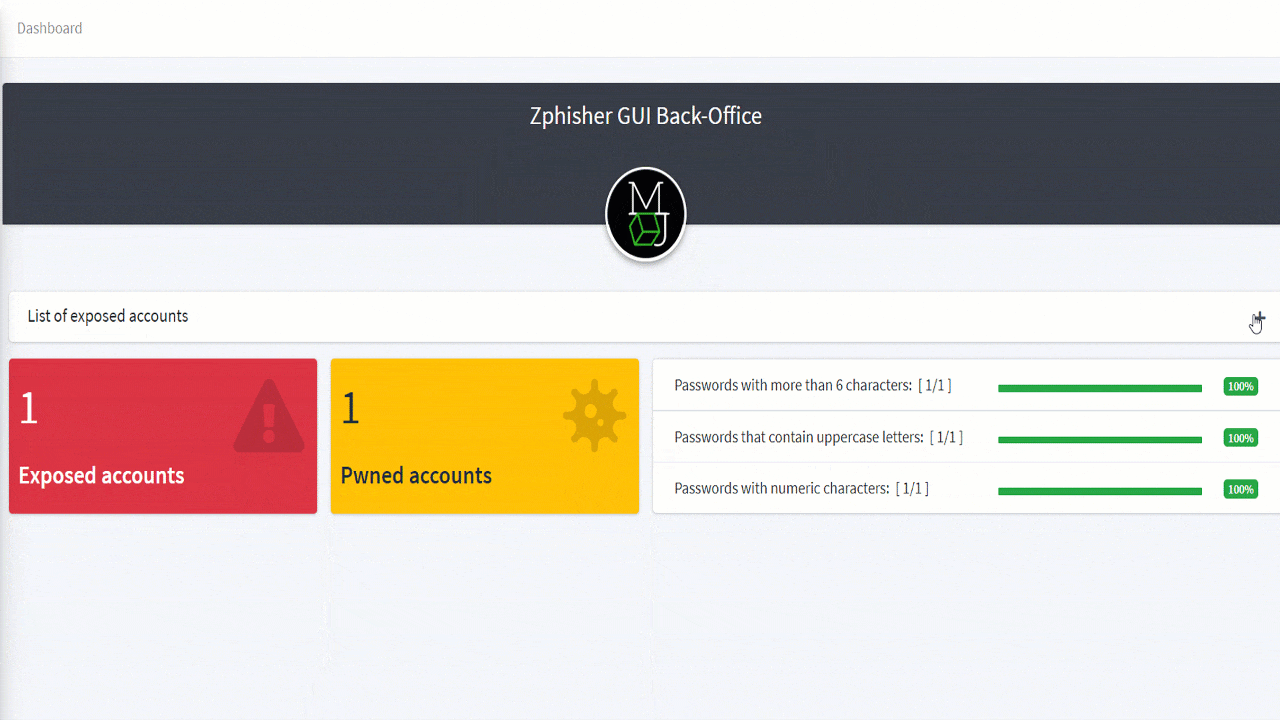
The Rise of Phishing Attacks and the Role of Tools Like Zphisher
January 15, 2025
4 min
Introduction to Phishing Attacks Phishing attacks have quickly become one of the most prevalent and dangerous threats[...]

Protecting Yourself from Everyday Cyber Threats
January 15, 2025
3 min
With technology woven into every aspect of our daily lives, protecting yourself from cyber threats is more[...]

Unraveling Encryption: The Guardian of Data Security
January 14, 2025
5 min
Data security is among the most pressing challenges in the digital age. With the exponential growth of[...]
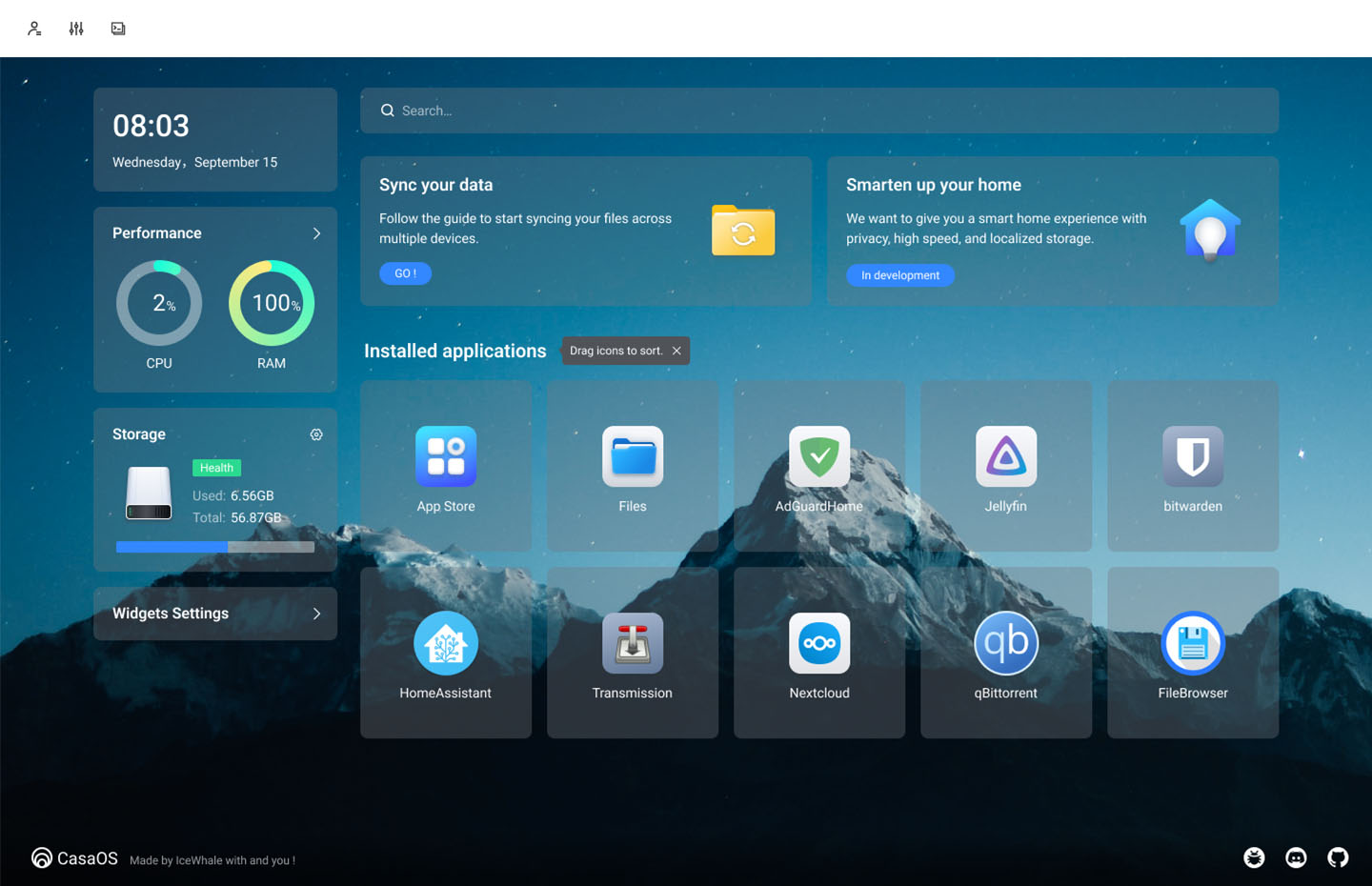
Building a Secure HomeLab with CasaOS
January 13, 2025
4 min
The digital landscape grows more complex every day, and staying ahead in cybersecurity has never been more[...]
Patching the Paradox: Securing Cyberspace with Third-Party Reliability
January 13, 2025
4 min
Cybersecurity is no longer a luxury; it’s a necessity. For organizations navigating the digital age, safeguarding sensitive[...]

TCP/IP Simplified: How Data Travels Across the Internet
January 12, 2025
4 min
Ever wondered how your messages or emails reach their destination within milliseconds? Think of it like sending[...]
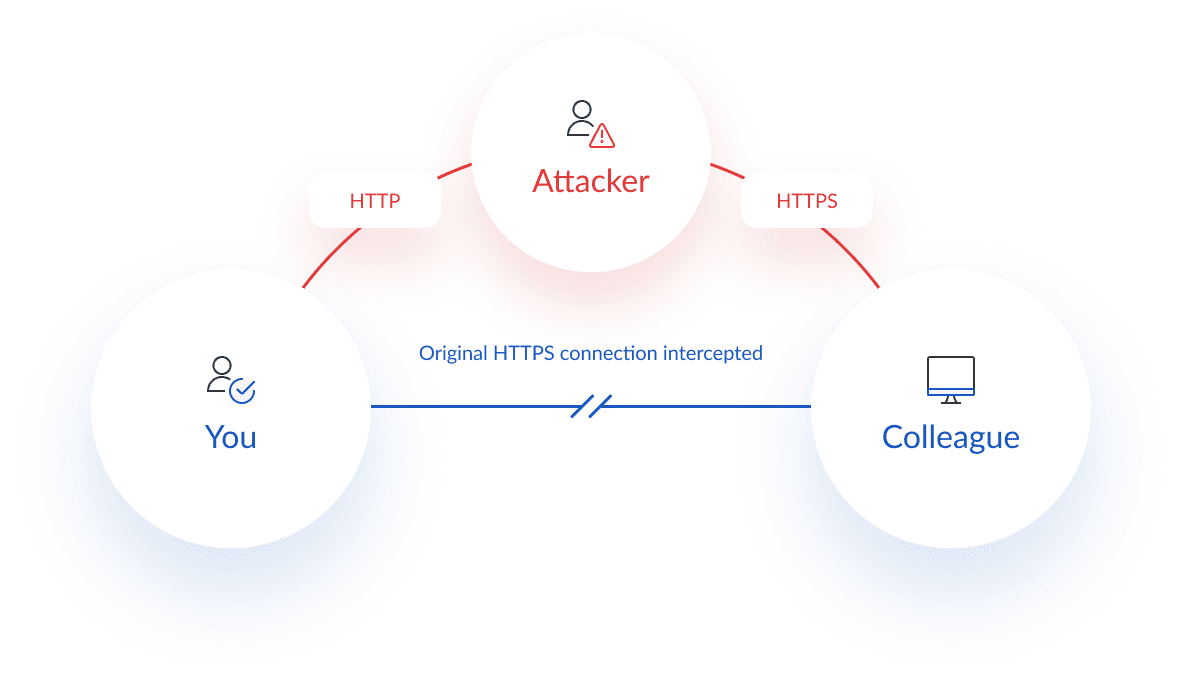
Understanding Man-in-the-Middle Attacks and How to Stay Safe
January 11, 2025
4 min
What are Man-in-the-Middle (MITM) Attacks? Man-in-the-Middle (MITM) attacks are one of the most common and dangerous cybersecurity[...]
Understanding DNS, Deep Packet Inspection, and the Battle Against Internet Censorship
January 10, 2025
4 min
Internet censorship has been a challenge since the very early days of the web. Yet, as the[...]

What is a Web Application Firewall? Why We Need to know
January 9, 2025
5 min
Web applications are the backbone of modern businesses, making them a prime target for cyber threats. For[...]

Biggest Cyber Attacks of 2024: Exploited Vulnerabilities and Lessons Learned
January 1, 2025
5 min
Cyberattacks have surged by 70% in 2024 (Source: Cybersecurity Ventures), signaling an escalating crisis that organizations across[...]

Proactive Cyber Threat Intelligence: Why Prevention Trumps Reaction
December 31, 2024
4 min
Cyberattacks are becoming increasingly costly for businesses. In just a year, the average cost of a data[...]

The Complete Roadmap to Land Your First Cybersecurity Job in 7-10 Months
December 20, 2024
5 min
Cybersecurity is one of the most in-demand career fields today, offering lucrative opportunities for those with the[...]

How to Secure Your Internet of Things (IoT) Devices
December 11, 2024
4 min
Did you know that approximately 98% of IoT device traffic is unencrypted? This shocking statistic shows just[...]

How to Protect Your Online Identity
December 11, 2024
5 min
The internet is an essential part of our lives, but it comes with risks. Identity theft and[...]

Top 10 Cybersecurity Threats Facing Businesses in 2024
December 11, 2024
4 min
Cybersecurity remains a critical concern for businesses in 2024. The global cost of cyberattacks is projected to[...]

The Essential Security Analyst Toolkit: Comprehensive Guide for SOC Professionals
December 10, 2024
4 min
Security Operations Center (SOC) analysts play a crucial role in protecting organizations from an ever-growing array of[...]

How to Lock Down Your Mobile Devices: The Ultimate Security Guide
December 9, 2024
4 min
Did you know that over 50% of mobile devices have unpatched vulnerabilities? This alarming statistic underscores how[...]

What is Ransomware and How to Protect Against It: A Comprehensive Guide
December 9, 2024
5 min
Understanding Ransomware Ransomware is a sophisticated form of malware designed to hold your data hostage, effectively locking[...]

The Ultimate Guide to Ethical Hacking: A Beginner’s Journey
December 8, 2024
4 min
The Ultimate Guide to Ethical Hacking: A Beginner's Journey In today's digital age, cybersecurity has become an[...]

How to Detect and Respond to a Data Breach: A Comprehensive Guide
December 7, 2024
5 min
Data breaches have become a significant threat to organizations and individuals alike. The consequences of these breaches[...]

The Importance of Regular Software Updates: Lessons from Real-World Cyber Attacks
December 6, 2024
4 min
The importance of regular software updates cannot be overstated. As cyber threats continue to evolve and become[...]

The Impact of AI on Cybersecurity
December 5, 2024
3 min
Cybersecurity has become a critical concern for individuals and organizations alike. As cyber threats evolve and become[...]

How to Protect Your Business from Cyber Fraud
December 1, 2024
6 min
Protecting your business from cyber fraud has become more crucial than ever. As technology advances, so do[...]

Create Your HomeLab for Cybersecurity
November 26, 2024
3 min
A home lab is a valuable tool for anyone interested in cybersecurity. It allows you to experiment[...]

Advanced Search Techniques
November 25, 2024
2 min
Google Dorks: The Power of Precision Searching Google Dorks, a technique that emerged around 2006-2007, is a[...]

Cybersecurity Roadmap for Beginners
November 18, 2024
3 min
Cybersecurity has become a cornerstone of digital safety, safeguarding individuals, organizations, and nations from ever-evolving threats. For[...]

The Importance of Using Strong, Unique Passwords
November 14, 2024
3 min
We rely heavily on various online platforms for work, entertainment, and daily life. From emails to banking[...]

How to Tell if Your Computer Has Been Hacked: A Practical Guide with Tools
November 9, 2024
5 min
With the rise in cyber threats, learning to recognize the signs of a hacked computer has become[...]

Dark Web and How It Works
October 26, 2024
3 min
The internet is vast and complex, with many layers that most everyday users never see. While we're[...]

Top 10 Cybersecurity Threats in 2024 and How to Mitigate Them
October 20, 2024
6 min
As we progress through 2024, the cybersecurity landscape is evolving rapidly, with new threats emerging and old[...]

Consider Removing Google from Your Life for Privacy
October 5, 2024
5 min
Google has become so embedded in our daily lives that the mere thought of removing it can[...]

AI-Generated Malware: The New Cyber Threat Everyone Should Know About
September 29, 2024
5 min
Imagine a world where the viruses attacking your computer aren't crafted by hackers but by machines. It[...]

How to Stay Anonymous Online: A Beginner’s Guide to Protecting Your Privacy
September 21, 2024
5 min
The idea of staying anonymous online has become more important than ever. You might think it’s easy[...]

Cybersecurity for Small Businesses: Best Practices
September 5, 2024
6 min
As a small business owner, it’s easy to think that only large corporations are targeted by hackers.[...]

Getting Started with Nmap: A Comprehensive Beginner’s Guide
August 12, 2024
5 min
Why Nmap is Essential Nmap is a network scanning tool that helps you discover devices, assess vulnerabilities,[...]

How to Create a Cyber Incident Response Plan: A Step-by-Step Guide
August 11, 2024
5 min
Cyber threats are more prevalent and sophisticated than ever before. Whether you're a small business owner or[...]

How VPNs Work: A Beginner’s Guide
August 10, 2024
6 min
Online privacy and security are more important than ever. You've probably heard of VPNs (Virtual Private Networks)[...]

How to Secure Your Home Network
August 9, 2024
6 min
Securing your home network is no longer a luxury—it’s a necessity. With an ever-increasing number of devices[...]

Understanding Phishing Attacks and How to Avoid Them
August 7, 2024
3 min
In the ever-evolving landscape of cybersecurity threats, phishing attacks remain one of the most prevalent and dangerous.[...]

How to Conduct a Personal OSINT Audit
August 6, 2024
3 min
What is OSINT? Open Source Intelligence (OSINT) involves collecting and analyzing publicly available information from various sources[...]

The Basics of Cybersecurity: A Beginner’s Guide
August 6, 2024
5 min
Cybersecurity has become more crucial than ever as our lives increasingly revolve around digital technology. Whether you're[...]

How to Secure Yourself Online: from OSINT Perspective
August 5, 2024
3 min
In today's digital age, online security is more critical than ever. With the increasing use of the[...]

What is OSINT? A Comprehensive Guide for Beginners
August 3, 2024
5 min
Open Source Intelligence (OSINT) is the process of collecting, analyzing, and utilizing publicly available information from various[...]

Essential Cybersecurity Resources for Professionals
July 31, 2024
4 min
As threats evolve, staying informed is crucial. Here's a comprehensive list of tools to enhance your cybersecurity[...]

A Comprehensive Guide to Starting Your Cybersecurity Career
July 31, 2024
4 min
Are you excited about starting a career in cybersecurity but feeling unsure where to begin? Cybersecurity offers[...]

How Long Does It Take for a Hacker to Crack a Password?
July 31, 2024
4 min
Securing your online accounts has never been more critical. With cyber threats continuing to evolve, strong passwords[...]
What Should You Do If You Receive a Suspicious Email
July 31, 2024
5 min
Phishing emails are one of the most common cybersecurity threats faced by individuals and businesses today. Cybercriminals[...]
The 8 Most Critical Windows Security Event IDs You Need to Monitor
July 31, 2024
4 min
When it comes to safeguarding your systems, staying ahead of potential threats is essential. For cybersecurity professionals,[...]

Top Cryptocurrency Hacks: Lessons in Cybersecurity
July 31, 2024
5 min
The cryptocurrency space has seen tremendous growth over the years, revolutionizing finance and attracting millions of users.[...]

The Truth About Linux Viruses and How to Protect Your System
July 31, 2024
5 min
For years, Linux users have embraced a sense of security, believing their systems were immune or significantly[...]

Enhancing Online Privacy: Choosing Between Tor and VPN
July 31, 2024
5 min
The Internet has become an integral part of our daily activities. Whether you're browsing for information, shopping[...]

DDoS Attacks! How to Stay Protected
July 31, 2024
4 min
A Distributed Denial of Service (DDoS) attack is one of the most common and disruptive cyber threats[...]
Exploring Shodan.io: A Powerful Tool in Cybersecurity
July 31, 2024
4 min
The field of cybersecurity continues to evolve, and the demand for powerful, effective tools that identify and[...]

How to Set Up a Cybersecurity Home Lab
July 31, 2024
5 min
Are you ready to get hands-on experience in cybersecurity? Setting up a cybersecurity home lab is one[...]

The Bangladesh Bank Heist: How Cybercriminals Exposed Vulnerabilities in Global Banking
July 31, 2024
4 min
In February 2016, the world was gripped by one of the most daring and sophisticated digital heists[...]
Unlocking the Power of Pi-hole in Cybersecurity Education
July 31, 2024
4 min
As the landscape of cybersecurity continues to evolve at a rapid pace, the need for practical, hands-on[...]

ESP8266: A Tiny WiFi Chip Powering Big IoT and Cybersecurity Innovations
July 31, 2024
4 min
The ESP8266, a small yet powerful low-cost chip, has revolutionized IoT (Internet of Things) projects by bringing[...]

Free Cybersecurity Courses: Save Thousands and Boost Your Career!
July 31, 2024
2 min
Presenting a list of FREE cybersecurity courses just for you! 💻 Seize this incredible opportunity to save[...]

Three Powerful Projects to Enhance Your Malware Analysis Skills
July 31, 2024
3 min
Deep Dive: Three Projects to Supercharge Your Malware Analysis Skills ✨ Malware analysis is an intricate art[...]

How to Recognize and Avoid Phishing Emails to Stay Secure
July 31, 2024
4 min
Phishing attacks are one of the most common tactics cybercriminals use to access sensitive information, such as[...]
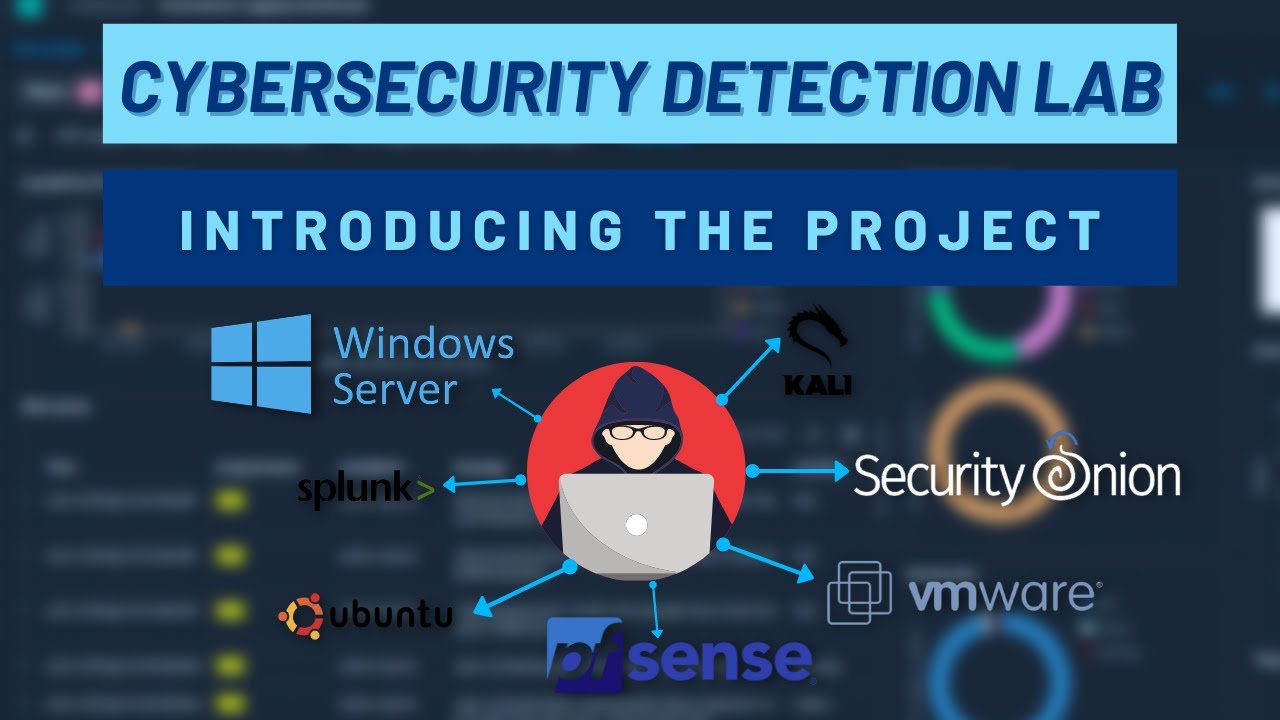
Building a Home Lab for Cybersecurity Beginners
July 31, 2024
5 min
Are you interested in a career in cybersecurity or simply passionate about exploring the field? A home[...]

IoT Security: Protecting Your Smart Devices and Data
July 31, 2024
5 min
Why IoT Security Matters The Internet of Things (IoT) is revolutionizing how we live, work, and interact[...]

The Fundamentals of Intrusion Detection Systems (IDS): How They Work and Why They’re Essential
July 31, 2024
5 min
Cybersecurity threats continue to evolve, making robust network protection more critical than ever. If you're looking to[...]

Protect your networks devices from cyber threats
July 31, 2024
4 min
Ensuring the security of your home devices and networks has become a top priority in today's hyper-connected[...]

Keep safe your kids from danger of internet
February 20, 2024
5 min
The internet is a double-edged sword. On one hand, it provides kids with access to a wealth[...]

How to Get into the Cybersecurity World
February 19, 2024
5 min
Cybersecurity is one of the fastest-growing and most sought-after industries today. With the rapid expansion of digital[...]

The Dual Nature of Shodan.io: Friend or Foe?
February 15, 2024
5 min
Cybersecurity is a fascinating field with endless learning opportunities. Even after nearly two decades in IT, I'm[...]

How to Stay Secure while using Public WiFi
January 1, 2024
5 min
Public Wi-Fi networks are everywhere—coffee shops, airports, libraries—offering convenient access to the internet on the go. But[...]

Cybersecurity awareness for parents
December 1, 2023
5 min
Cybersecurity is the practice of protecting devices, networks, and sensitive information from cyber attacks, unauthorized access, and[...]

5 Tips for Keeping Your Kids Safe Online
November 11, 2023
5 min
The internet has become an integral part of our lives, offering kids access to incredible opportunities, knowledge,[...]

Roadmap for Teaching Cybersecurity to Kids
October 22, 2023
6 min
The digital world is evolving rapidly, with kids spending more and more time online—from playing games and[...]

Everything about Ransomware
July 31, 2023
4 min
Ransomware is one of the fastest-growing cybersecurity threats, affecting individuals and organizations across the globe. It’s a[...]

Teach children about cybersecurity
July 31, 2023
4 min
With technology playing an integral role in our daily lives, teaching children about cybersecurity has never been[...]
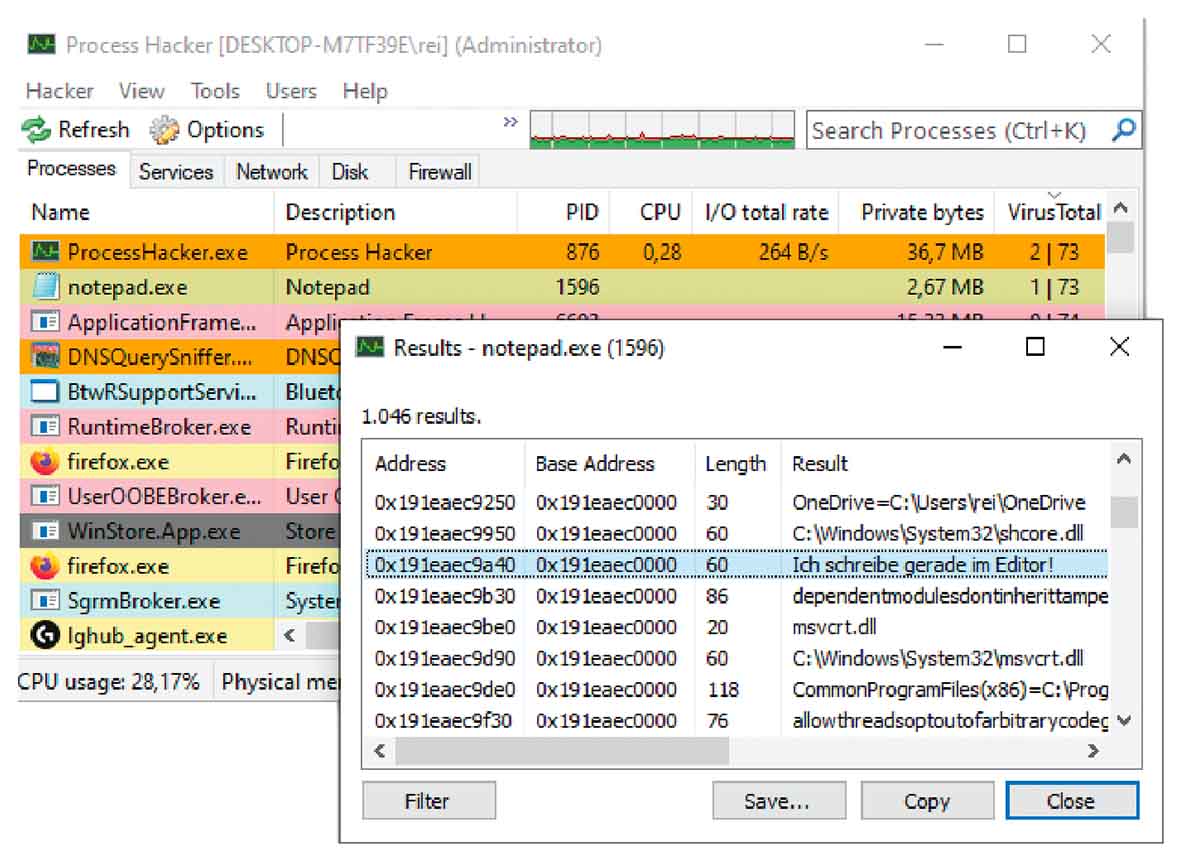
Processes that are running on a computer can be malicious
July 31, 2023
4 min
With every click, download, and file opened, your computer is exposed to potential cyber threats. Malicious processes[...]

What are IoCs of RANSOMWARE on the endpoints?
April 30, 2023
4 min
Ransomware attacks continue to be one of the most pressing cybersecurity threats of our time. These attacks,[...]

How can I determine if my computer is infected?
March 31, 2023
5 min
Cybersecurity threats are more prevalent than ever, making it crucial for individuals—especially students and learners in the[...]